4.2.3 Security Hardening
Preface
Document Version History
- v1.0 – initial public release on oscarmanual.org – May 9, 2010
- v1.1 – corrections to Tomcat configuration – June 2, 2010
- v1.2 – ported to new.oscarmanual.org – June 26, 2010
- v1.3 – updated for version 10_06 – July 1, 2010
- v1.4 – added screen shot – Aug 23, 2010
- v1.5 – added amendment to allow local http access to drugref – Aug 31, 2010
- v1.6 – added whole disk encryption – June 19, 2011
- v1.7 – dropped SQL to expire default credentials as this is now in the install scripts – Aug 30, 2011
- v1.8 – added information to support printing and faxing on non standard ports – Sept 7, 2012
|
Contents
|
Prerequisites
It is assumed that- You have the Ubuntu 10.4 LTS "Lucid" alternate installation CD
- You have a basic level of Linux knowledge
- You can open a Linux terminal
- You can use a Linux text editor
- You can cut and paste EXACTLY the following instructions
Level One Defences: SSL
Level One Defenses are necessary if you do not expose Oscar to the internet but have a network where a machine can be compromised.
TIP: New installs of Oscar 12_1 Build 48 and above can be configured to automatically setup SSL connections for Oscar
Set up Tomcat to use SSL connections
SSL, or Secure Socket Layer, is a technology which allows web browsers and web servers to communicate over a secured connection. This has several security advantages
- The sever presents authentication to the user as a "Certificate", as proof the site is who and what it claims to be.
- The data being sent is encrypted by one side, transmitted, then decrypted by the other side before processing
a) Prepare a Certificate
Use the Java keytool to generate a key for tomcat using standard RSA encryption. Don't use the password changeit that is shown but do use the same password for both the keypass and the storepass for Tomcat 6 or earlier.
sudo $JAVA_HOME/bin/keytool -genkey -alias tomcat -validity 3650 -keyalg RSA-keystore/etc/tomcat6/.keystore-keypass changeit -storepass changeit
You will be prompted for your name (your server IP or domain), organisational unit (clinic), organisation (.), city, province and country. The result is a hidden .keystore file in the /etc/tomcat6 directory.
b) Edit Tomcat Configuration
The
final step is to configure the Connector for the
Tomcat 6 instance.sudo nano $CATALINA_BASE/conf/server.xmlAdd the following code
<Connector port="8443" protocol="HTTP/1.1"
SSLEnabled="true"
maxThreads="200"
scheme="https"
secure="true"
enableLookups="false"
disableUploadTimeout="true"
clientAuth="false"
sslProtocol="TLS"
keystoreFile="/etc/tomcat6/.keystore"
keystorePass="changeit" /><Connector port="8080" protocol="HTTP/1.1"
address="127.0.0.1"
connectionTimeout="20000"
URIEncoding="UTF-8"
redirectPort="8443"/>
Remove or comment out the following default connector that is less secure, unless you need it (You might, usually for integration with the native webserver, eg the Apache Http server).
<Connector port="8009" protocol="AJP/1.3" redirectPort="8443" /Now restart Tomcat
sudo /etc/init.d/tomcat6 restartIf you have installed Oscar locally with the instructions in 6.1 you should be able to login to Oscar at https://localhost:8443/oscar otherwise substitute localhost with the IP for the Oscar server.
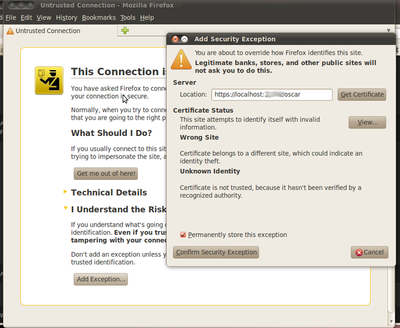
Note that the browser will be concerned about the validity of the Certificate (after all anyone could have signed it!) so you will have to add an exception for the browser to let you access the Oscar webpages. This varies by browser. For Firefox 3.x click on "I Understand the Risks" > Add Exemption > Confirm Security Exemption
Troubleshooting and Tweaks
If you mess up the keytool and want to try again you will need to delete the tomcat keytool that you stored
sudo keytool -delete -alias tomcat -keystore /etc/tomcat6/.keystore
If you need to extract the public key for export to say /etc/tomcat6/tomcat.cer
sudo $JAVA_HOME/bin/keytool -export -alias tomcat -file /etc/tomcat6/tomcat.cer -keystore /etc/tomcat6/.keystore -storepass changeit
Oscar printing to pdf and faxing assumes that you have configured https on port 8443. You can configure other ports to work (eg 88443) by adding the following property value to oscar_mcmaster.properties (or similar named file)
oscar_port=88443
Level Two Defences Full Disc Encryption
An option in the "alternate cd" installation of Ubuntu is to encrypt the entire hard drive. This will make it very difficult for a thief to access your data even if they physically steal the server (physical theft or access is usually enough to steal data, even in linux) Note that full disc encryption doesn't protect you from: "Cold Boot Attacks Against Disk Encryption"or "Weak password brute force."
To set up full disc encryption in Ubuntu 10.04 LTS you use the alternate cd and select full disc encryption as below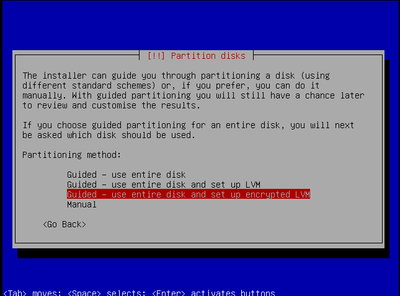
Level Three Defences Secure SSH
Most Linux servers are remotely managed by SSH login. Thus the most common type of attack is by trying to login to your ip on port 22.
Disable SSH root login, and require a key for SSH access to the box
vi /etc/ssh/sshd_config
And add following entries
PermitRootLogin no PasswordAuthentication yes
That still has your port dealing with login attempts that the box has to (eventually) deny. Install denyhosts to keep them out the door.
sudo apt-get install denyhosts
Level Four Defences Harden Tomcat 6
If you want to access Oscar from the Internet it is probably best if you form a tunnel and use SSH access to Oscar.If you actually have to expose your production box to the raw Internet then you should further reduce the ways that your box will be attacked. First remember that the more services that are running on the server the more ways it can be attacked. If possible disable other deamons and services or remove to another machine. Then make sure that Tomcat has the least number of loose ends available to be targeted.
Prune Tomcat of Unused
Resources
Remove extraneous Tomcat resources:
rm -rf $CATALINA_HOME/webapps/js-examples $CATALINA_HOME/webapps/servlet-example $CATALINA_HOME/webapps/webdav \
$CATALINA_HOME/webapps/tomcat-docs $CATALINA_HOME/webapps/balancer $CATALINA_HOME/webapps/ROOT/admin $CATALINA_HOME/webapps/examplescd $CATALINA_HOME/lib
sudo jar xf catalina.jar org/apache/catalina/util/ServerInfo.propertiesNavigate to the util directory that was created and open ServerInfo.properties in an editor
cd org/apache/Catalina/utilsudo vi ServerInfo.properties
Update the following attributes from something like the defaults below to anything else...
server.number=6.0.26.0
server.info=Apache Tomcat/6.0
server.built=Jul 8 2009 11:40:35sudo chown tomcat6.tomcat6 $CATALINA_HOME sudo chown tomcat6.tomcat6 $CATALINA_BASE sudo chown tomcat6:tomcat6 $CATALINA_HOME/conf sudo chown tomcat6:tomcat6 $CATALINA_HOME/logs sudo chown tomcat6:tomcat6 $CATALINA_HOME/temp sudo chown tomcat6:tomcat6 $CATALINA_HOME/bin sudo chown tomcat6:tomcat6 $CATALINA_HOME/webapps sudo chown tomcat6:tomcat6 $CATALINA_HOME/conf/catalina.policy sudo chown tomcat6:tomcat6 $CATALINA_HOME/conf/catalina.properties sudo chown tomcat6:tomcat6 /etc/tomcat6/policy.d sudo chown tomcat6:tomcat6 $CATALINA_HOME/conf/context.xml sudo chown tomcat6:tomcat6 $CATALINA_HOME/conf/logging.properties sudo chown tomcat6:tomcat6 $CATALINA_HOME/conf/server.xml sudo chown tomcat6:tomcat6 $CATALINA_HOME/conf/tomcat-users.xml sudo chown tomcat6:tomcat6 $CATALINA_HOME/conf/web.xml sudo chmod g-w,o-rwx $CATALINA_HOME/conf/web.xml sudo chmod g-w,o-rwx $CATALINA_HOME/conf/tomcat-users.xml sudo chmod g-w,o-rwx $CATALINA_HOME/conf/server.xml sudo chmod g-w,o-rwx $CATALINA_HOME/conf/logging.properties sudo chmod g-w,o-rwx $CATALINA_HOME/conf/context.xml sudo chmod 770 /etc/tomcat6/policy.d sudo chmod 770 $CATALINA_HOME/conf/catalina.policy sudo chmod g-w,o-rwx $CATALINA_HOME/conf/catalina.properties sudo chmod g-w,o-rwx $CATALINA_HOME/webapps sudo chmod g-w,o-rwx $CATALINA_HOME/bin sudo chmod o-rwx $CATALINA_HOME/temp sudo chmod o-rwx $CATALINA_HOME/logs sudo chmod g-w,o-rwx $CATALINA_HOME/conf sudo chmod g-w,o-rwx $CATALINA_BASE sudo chmod g-w,o-rwx $CATALINA_HOME
Use Client Side
Authentication (untested)
We usually use SSL technology
just to encrypt traffic to and from the server. However the server can
be also be configured to ask for authentication of the client (user)sudo vi $CATALINA_HOME/conf/server.xml<Connector port="8443" protocol="HTTP/1.1"
SSLEnabled="true"
maxThreads="200" scheme="https" secure="true"
enableLookups="false"
disableUploadTimeout="true"
clientAuth="true"
sslProtocol="TLS"
keystoreFile="/etc/tomcat6/.keystore"
keystorePass="changeit" />To create a keystore named client-keystore.jks that contains a client certificate named client.cer, generate the client certificate.
sudo $JAVA_HOME/bin/keytool -genkey -alias client-alias -keyalg RSA -keypass changeit -storepass changeit -keystore keystore.jkssudo $JAVA_HOME/bin/keytool -export -alias client-alias -storepass changeit -file client.cer -keystore keystore.jkssudo $JAVA_HOME/bin/keytool\bin\keytool -import -v -trustcacerts-alias client-alias -file client.cer-alias client-alias -file client.cer-keystore <J2EE_HOME>/domains/domain1/config/cacerts.jks-keypass changeit -storepass changeit
Document Actions

